This post will talk about the basic understanding of TLS-PSK protocol. It will not cover TLS's history and how its mathematical algorithms work. Instead, what is TLS-PSK protocol and how it works will be discussed here. I prefer using diagrams to help explain things. Hopefully, it can give readers a very basic insights of TLS-PSK.
What is TLS-PSK
Before talking about what is TLS-PSK, I would like to introduce what is TLS first. TLS, Transport Layer Security, is a cryptographic protocol, aims to provide protection to end-to-end communication over the internet. It helps to protect network users from eavesdropping, tempering and so on.
Clear data transmission is dangerous, given that technical hacker can listen to the communication between two computers and steal sensitive data like user name, password and so on. This is situation where TLS can step in and protect you.
TLS has two steps: TLS handshake and data transmission. During TLS handshake, the communicating parties must agree on an session key and a cipher suite. This session key will be used to encrypt communication data until connection closes. But how to make sure the the two parties are using the same session key, or how to exchange the session key securely between them. There are many methods to do key exchange, TLS-PSK(Pre-Shared Key) is one of them. And it is a fast one, because it uses symmetric key algorithm and improve the performance. So it is usually used in embedded systems which usually have limited CPU power.
How does TLS-PSK work
TLS-PSK protocol uses symmetric keys as pre-shared key to exchange session keys. There are three cipher suites for TLS-PSK: symmetric key only authentication, DH key exchange authenticated with a pre-shared key and public key authentication. In this post, we will only talk about the symmetric key only PSK.
Before the handshake start, the session keys are already known by both communicating parties, because session key are derived from the pre-shared key, and pre-shared key is known by both. You may want to ask how pre-shared key is distributed. Well, there are many mechanisms used to share the pre-shared keys like GBA(Generic BootStrapping Architecture), which we will not talk about in this post. So since the session keys are already known before handshake, then why we still need to do handshake. Because we need to make sure the session keys to be used are the same, otherwise it will failed to do communication in application level. Besides, there are could be many keys stored in server, server needs to know which key to use. So usually during handshake, the client will send ClientKeyExchange request with PSK Identity to tell server which key to use.
Then how does TLS-PSK handshake works exactly, what are the steps. So in the following, I will use simplified diagrams to illustrate the TLS-PSK handshake process. Detail will not be discussed in each step. We can refer to RFC standard for the details.
1, Client sends a ClientHello message to server to initiate the communication;
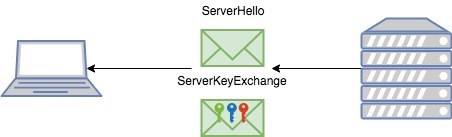
2, Server sends back a ServerHello message and ServerKeyExchange message. The ServerKeyExchange message will contain the session key hint, which helps to tell client what key labels server has; (Note, represents a key label, not the actual session key, the actual key is
represents a key label, not the actual session key, the actual key is  )
)
3, After client confirms server has the same key label it wants to use. Then it will send a Finished message with ClientKeyExchange, which is encrypted by the session key with key label , and in the ClientKeyExchange message, it specifies which key label
, and in the ClientKeyExchange message, it specifies which key label to use;
to use;
4, Server receives the Finished message, and get the key label from ClientKeyExchange, get the actual session key based on key label
based on key label , then use session key
, then use session key to decrypt the finished message;
to decrypt the finished message;
5, If decryption is successful, then send another finished message. On the client's side, it will repeat the same processor as step 4 since it knows which key to use;
6, If the decryption is passed too. Then the TLS-PSK handshake is done. Client and server can start to use the same session key to secure their communication on the application level.
Summary
So TLS-PSK is one of the TLS key exchange algorithms. It is simpler and faster compared to other asymmetric key exchange algorithms. You can find the details on RFC[4] standard.
(The elements in parenthesis are not included when the PSK key exchange algorithm is used. and "*" indicates a situation-dependent message that is not always sent [RFC 4])
What is TLS-PSK
Before talking about what is TLS-PSK, I would like to introduce what is TLS first. TLS, Transport Layer Security, is a cryptographic protocol, aims to provide protection to end-to-end communication over the internet. It helps to protect network users from eavesdropping, tempering and so on.
Clear data transmission is dangerous, given that technical hacker can listen to the communication between two computers and steal sensitive data like user name, password and so on. This is situation where TLS can step in and protect you.
TLS has two steps: TLS handshake and data transmission. During TLS handshake, the communicating parties must agree on an session key and a cipher suite. This session key will be used to encrypt communication data until connection closes. But how to make sure the the two parties are using the same session key, or how to exchange the session key securely between them. There are many methods to do key exchange, TLS-PSK(Pre-Shared Key) is one of them. And it is a fast one, because it uses symmetric key algorithm and improve the performance. So it is usually used in embedded systems which usually have limited CPU power.
How does TLS-PSK work
TLS-PSK protocol uses symmetric keys as pre-shared key to exchange session keys. There are three cipher suites for TLS-PSK: symmetric key only authentication, DH key exchange authenticated with a pre-shared key and public key authentication. In this post, we will only talk about the symmetric key only PSK.
Before the handshake start, the session keys are already known by both communicating parties, because session key are derived from the pre-shared key, and pre-shared key is known by both. You may want to ask how pre-shared key is distributed. Well, there are many mechanisms used to share the pre-shared keys like GBA(Generic BootStrapping Architecture), which we will not talk about in this post. So since the session keys are already known before handshake, then why we still need to do handshake. Because we need to make sure the session keys to be used are the same, otherwise it will failed to do communication in application level. Besides, there are could be many keys stored in server, server needs to know which key to use. So usually during handshake, the client will send ClientKeyExchange request with PSK Identity to tell server which key to use.
Then how does TLS-PSK handshake works exactly, what are the steps. So in the following, I will use simplified diagrams to illustrate the TLS-PSK handshake process. Detail will not be discussed in each step. We can refer to RFC standard for the details.
1, Client sends a ClientHello message to server to initiate the communication;
2, Server sends back a ServerHello message and ServerKeyExchange message. The ServerKeyExchange message will contain the session key hint, which helps to tell client what key labels server has; (Note,
 represents a key label, not the actual session key, the actual key is
represents a key label, not the actual session key, the actual key is  )
)3, After client confirms server has the same key label it wants to use. Then it will send a Finished message with ClientKeyExchange, which is encrypted by the session key with key label
 , and in the ClientKeyExchange message, it specifies which key label
, and in the ClientKeyExchange message, it specifies which key label to use;
to use;4, Server receives the Finished message, and get the key label from ClientKeyExchange, get the actual session key
 based on key label
based on key label , then use session key
, then use session key to decrypt the finished message;
to decrypt the finished message;5, If decryption is successful, then send another finished message. On the client's side, it will repeat the same processor as step 4 since it knows which key to use;
6, If the decryption is passed too. Then the TLS-PSK handshake is done. Client and server can start to use the same session key to secure their communication on the application level.
Summary
So TLS-PSK is one of the TLS key exchange algorithms. It is simpler and faster compared to other asymmetric key exchange algorithms. You can find the details on RFC[4] standard.
(The elements in parenthesis are not included when the PSK key exchange algorithm is used. and "*" indicates a situation-dependent message that is not always sent [RFC 4])






Very well explained, Thanks!
ReplyDeleteCrystal clear explanation about TLS-PSK. Please add more pages explaning the DH and public key based methods as well.
ReplyDelete